How we use the 1Password SSH Agent for SSH Key Security
As web application developers and security professionals, managing SSH keys securely is crucial. The 1Password SSH Agent enhances security by integrating SSH key management within the 1Password and MacOS ecosystem.
At Si Novi, we use the 1Password SSH Agent to keep our keys secure and easily accessible, ensuring that our development workflows are both safe and efficient.
Why We Chose the 1Password SSH Agent
For us, centralising our SSH key management in 1Password was an easy choice. By storing our keys in encrypted vaults in 1Password, we eliminate the risks associated with scattered or misplaced keys. This centralisation allows us to maintain consistent security practices, ensuring that every team member adheres to the same high standards.
Traditional SSH Key Management
Before using the 1Password SSH Agent, like many developers, we used SSH keys from the local ~/.ssh directory. This approach, while standard, has its vulnerabilities. The ~/.ssh directory on a developer's machine is where private and public keys are typically stored. If a machine is compromised or accessed by an unauthorised person, these keys could be exposed, leading to potential security breaches. Managing multiple keys across different machines also became cumbersome, with the risk of keys being lost, duplicated, or improperly secured.
Use-cases for using SSH keys with 1Password SSH Agent
GitHub Commit Signing and Repository Access
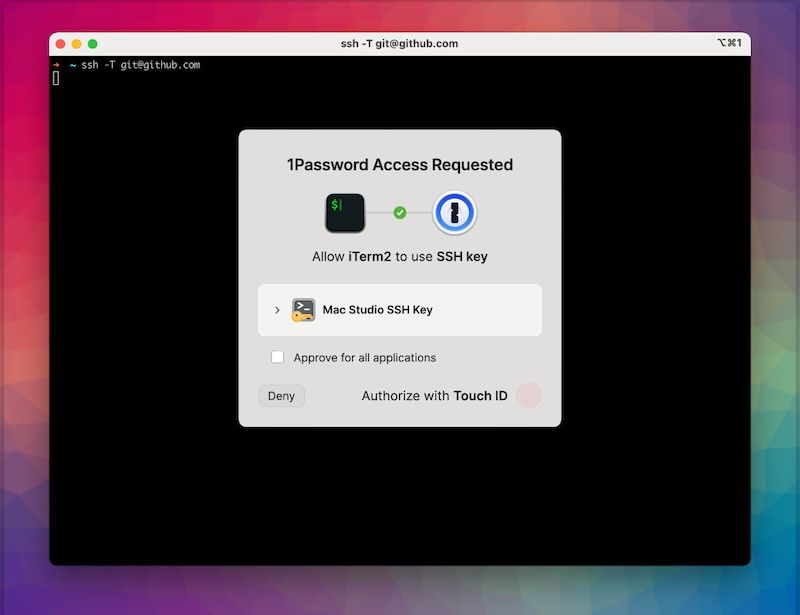
For developers using Git, signing commits is useful for maintaining code integrity. At Si Novi, we rely on the 1Password SSH Agent to provide our own SSH key when using git commands, to sign our commits and verify the authenticity of commits in our repositories. When pushing changes to GitHub, the agent prompts us to authenticate using biometric Touch ID.
This means our while private keys remain encrypted and never leave the safety of 1Password, we can still use them easily to ensure that our commits are signed and our access to cloud repositories is secure.
SSH Access to Servers
Accessing remote servers is a regular part of our work. Whether we're managing AWS EC2 instances or other servers, the 1Password SSH Agent ensures that our SSH keys are securely stored and accessed. Instead of keeping keys on our local machines, we let 1Password handle them.
When connecting to a server with a command like ssh ec2-user@1.2.3.4, the 1Password SSH Agent automatically provides the correct key, protected by biometric authentication.
Collaborative Development
When necessary to share an SSH key amongst multiple people, sharing it securely is essential. The 1Password SSH Agent allows us to share specific keys among team members securely, and to have a single source of truth for each key.
Keys can be shared in specific 1Password vaults, ensuring that only the intended recipient can access it. This feature helps us maintain strict control over our SSH resources while allowing smooth collaboration between us.
Revoking or changing a key becomes an easy process with only one place to make the change - all users of that key then pick up the new key through 1Password.
Project management and key switching
Managing multiple projects means holding and managing many different SSH keys. However because OpenSSH agents operate by offering all available keys in turn to the client, if you have lots of keys, you can hit the default 6-key limit and be unable to connect to a server.
By leveraging the standard SSH config protocols it's possible to configure the 1Password agent to understand which key is for which host, allowing us to work past the usual 6-key limit and futher ensure that only specific keys are enabled for use. This is done by using the public key as an Identity File, and defining the Host identity in your SSH config file.
An example configuration for the ~/.ssh/config file could be as follows:
Host my-server
HostName 12.34.56.78
User ec2-user
IdentityFile ~/.ssh/my-server-public-key.pub
IdentitiesOnly yesWhich then allows you to perform ssh my-server and automatically pick up the correct key via the 1Password SSH Agent
Differences from the OpenSSH Agent
The traditional OpenSSH agent (ssh-agent) found on most systems requires manual key management. After launching, you must add your keys with ssh-add, making them available for any process, and it's up to the user to remove them when no longer needed.
In contrast, the 1Password SSH Agent takes a more secure approach. Instead of adding or removing keys manually, it automatically makes all eligible keys stored in 1Password available for SSH, but only with your explicit consent each time a key is used. This means your private keys are never accessed without your approval.
The benefits we've experienced
Since adopting the 1Password SSH Agent, we've seen significant improvements in both security and operational efficiency. The encrypted storage and biometric authentication provide us with peace of mind, knowing that our SSH keys are well protected. Additionally, the streamlined workflow allows us to focus on what we do best - developing and deploying high-quality web applications - without being hamstrung by SSH file management and the manual security overhead.
Conclusion
At Si Novi, the 1Password SSH Agent has become an integral part of our security strategy.
It provides a reliable and convenient way to manage SSH keys, integrating seamlessly with our MacOS environments.
Whether we're pushing code to GitHub, accessing servers, or collaborating on projects, the 1Password SSH Agent ensures that our keys are safe, our workflows are smooth, and our security standards are upheld. In an increasingly complex digital landscape, it's a tool we trust to keep our development environment secure and efficient.